

Security cache system
The security cache system temporarily stores security objects such as users, roles, groups and ACLs. ACL, short for Access Control List, is the core object of the security authorization system, and is in charge of storing and checking principal permissions. When JReport Server requires information from the security system, it can fetch it from the cache for better performance.
The cache system caches not only security objects for the built-in security system, but also those implemented by the Security API from the external security system. It caches security information in the security data. If the security service needs security information, it will fetch it from the security data. However, if the security data cannot find the information, it will request it from the Security API, and then cache it in the cache system. When the security information is modified in the security system, the Security API is invoked directly in order to modify the security data.
Note: There is a special interface SecurityListener in the cache system, through which the cache is noted to update the cached information. It is recommended that you invoke it when you access the external security system, so as to synchronize security data between the cache system and the external security system.
The following focuses on the configuration and synchronization of the security cache system.
Configuring the security cache system
The security cache system enables you to define the maximum number of users, roles, groups and ACL objects that can be cached. There are three ways in which you can customize the security cache system as explained below:
Configuring by editing the server.properties file
Edit the following four properties:
- server.security.user.cache.size
This should be an integer value. Its value indicates the maximum number of user objects that the security cache can store. The default value is 1000.
- server.security.role.cache.size
This should be an integer value. Its value indicates the maximum number of role objects that the security cache can store. The default value is 50.
- server.security.group.cache.size
This should be an integer value. Its value indicates the maximum number of group objects that the security cache can store. The default value is 50.
- server.security.protection.cache.size
This should be an integer value. Its value indicates the maximum number of ACL objects that the security cache can store. The default value is 100.
For instance,
- If server.security.user.cache.size=1000, the cache can then store at most 1000 user objects.
- If server.security.role.cache.size=100, the cache can then store 100 role objects.
- If server.security.group.cache.size=100, the cache can then store 100 group objects.
- If server.security.protection.cache.size=100, the cache can then store 100 ACL objects.
Configuring from the JReport Administration page
You must be a member of the administrator role in order to access the JReport Administration page.
- Log onto the JReport Administration page, click Cache on the system toolbar, and then select Security Cache from the drop-down menu.
- In the Security Cache panel, four options are provided for specifying the cache size:
- User Cache Size
The maximum number of user objects that the security cache can store. Should be an integer value.
- Role Cache Size
The maximum number of role objects that the security cache can store. Should be an integer value.
- Group Cache Size
The maximum number of group objects that the security cache can store. Should be an integer value.
- Protection Cache Size
The maximum number of ACL objects that the security cache can store. Should be an integer value.
- When done, click Save to apply the settings.
Configuring using the API method
Invoke the following methods in the API class jet.server.api.admin.cfg.ConfigurationAdvanced:
/**
* Set the security user cache's size
* Setting the size of the cache to zero or negative means closing the security user cache.
* @param size
*/
public void setSecurityUserCacheSize(int size);
/**
* Get the size of the security user cache
* @return the size of the security user cache
*/
public int getSecurityUserCacheSize();
/**
* Set the size of the security role cache
* Setting the size of the cache to zero or negative means closing the security role cache
* @param size
*/
public void setSecurityRoleCacheSize(int size);
/**
* Get the size of the security role cache
* @return the size of the security role cache
*/
public int getSecurityRoleCacheSize();
/**
* Set the size of the security group cache
* Setting the size of the cache to zero or negative means closing the security group cache
* @param size
*/
public void setSecurityGroupCacheSize(int size);
/**
* Get the size of the security group cache
* @return the size of the security group cache
*/
public int getSecurityGroupCacheSize();
/**
* Set the size of the security protection cache
* Setting the size of the cache to zero or negative means closing the security protection cache
* @param size<
*/
public void setSecurityProtectionCacheSize(int size);
/**
* Get the size of the security protection cache
* @return the size of the security protection cache
*/
public int getSecurityProectionCacheSize();
|
Synchronizing the security cache system
A synchronization system has been provided for synchronizing JReport Server's security system with your external security systems. When the security cache system receives a security information modification event, it will then fetch the security information from the API and update the cached information.
The following is a diagram of the synchronization system mechanism:
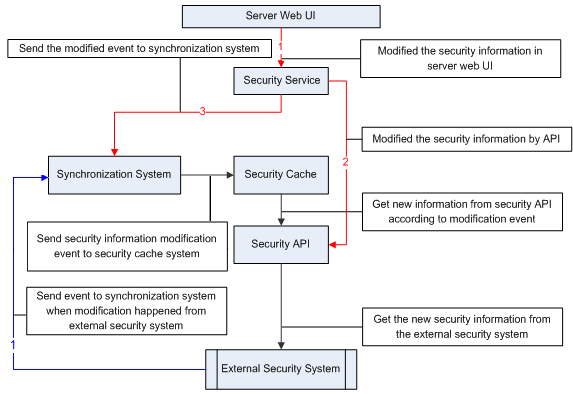
There are two ways to invoke the synchronization system. The first is to modify the security information on our Server web UI (red line), and the second is to modify the external security system (blue line).




